About
Kerberos credentials, or “tickets” are the credentials in Kerberos.
There are only two different types for tickets that the KDC issues.
- Ticket Granting Ticket (TGT). The first ticket obtained is a ticket-granting ticket (TGT), which permits to obtain additional service tickets.
Articles Related
Management
Storage
Kerberos tickets may be stored in a file, or they may exist only in memory. The storage is also called cache
Cache
Delete
The kdestroy utility destroys the user’s active Kerberos authorization tickets by writing zeros to the specified credentials cache that contains them.
Get
Automatic
If your site is using the Kerberos V5 login program, you will get Kerberos tickets automatically when you log in otherwise, you need to explicitly obtain them.
kinit
Using the kinit program, you can obtain and cache Kerberos ticket-granting tickets.
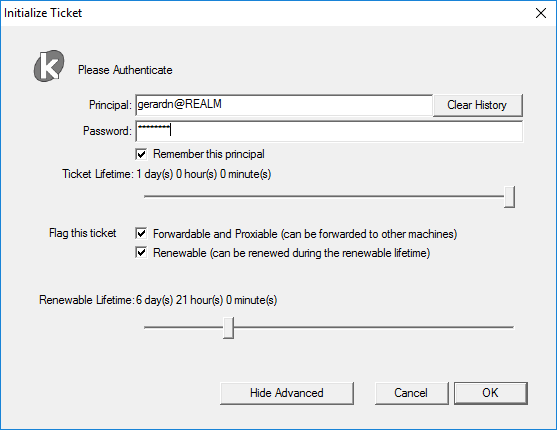
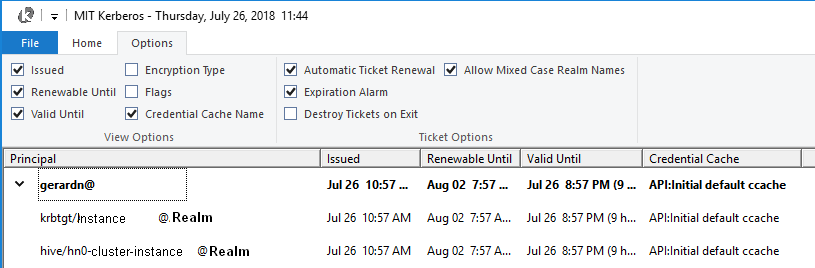
MIT Kerberos Ticket Manager
After a windows mit installation, you can obtain a ticket with your password and the MIT Kerberos Ticket Manager application.
where:
- the default values comes from the krb5 conf file
[libdefaults]
renew_lifetime = 7d
forwardable = true
default_realm = REALM
ticket_lifetime = 30d
dns_lookup_realm = false
dns_lookup_kdc = false
udp_preference_limit = 1
List
klist
- klist permits to see the ticket with their flags.
klist
Current LogonId is 0:0x295aab
Cached Tickets: (3)
#0> Client: gerardn @ DOMAIN20.LOCAL
Server: krbtgt/DOMAIN20.LOCAL @ DOMAIN20.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40e10000 -> forwardable renewable initial pre_authent name_canonicalize
Start Time: 7/26/2018 9:34:57 (local)
End Time: 7/26/2018 19:34:57 (local)
Renew Time: 8/2/2018 9:34:57 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0x1 -> PRIMARY
Kdc Called: myKdc.gerardnico.com
#1> Client: gerardn @ DOMAIN20.LOCAL
Server: ldap/shrwdc0002p.domain20.local @ DOMAIN20.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 7/26/2018 9:35:02 (local)
End Time: 7/26/2018 19:34:57 (local)
Renew Time: 8/2/2018 9:34:57 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called: myKdc.gerardnico.com
#2> Client: gerardn @ DOMAIN20.LOCAL
Server: LDAP/shrwdc0003p.domain20.local/domain20.local @ DOMAIN20.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 7/26/2018 9:35:02 (local)
End Time: 7/26/2018 19:34:57 (local)
Renew Time: 8/2/2018 9:34:57 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called: myKdc.gerardnico.com
ticket manager list
- The Windows MIT ticket manager utility also
Flag
You can use the (flag|properties) with the klist utility and the -f option (f means flag).
forward
A new ticket can be issued with a different network address.
This allows for authentication forwarding. For example, if a user with a forwardable TGT logs into a remote system, the KDC could issue a new TGT for that user with the netword address of the remote system, allowing authentication on that host to work as though the user were logged in locally.
proxy
Security - (Proxy|N-tier|Impersonation) authentication in Kerberos.
A proxiable ticket is similar to a forwardable ticket in that it allows a service to take on the identity of the client.
Unlike a forwardable ticket, however, a proxiable ticket is only issued for specific services. In other words, a ticket-granting ticket (TGT) cannot be issued based on a ticket that is proxiable but not forwardable.